Lei Feng network (search "Lei Feng Net" public concern) : Original author of this article clouds.

In March, when the US Department of Defense announced that it had partnered with HackerOne to invite hackers to participate in the "Hack the Pentagon" vulnerabilities program , HackerOne once again became the focus of the industry. For rookies that have been caught up in various loopholes at home and abroad, they have written about HackerOne in terms of their personal opinions and capabilities.
| HackerOne IntroductionHackerOne is a vulnerability testing company headquartered in San Francisco, USA. The company is located in Groningen, the Netherlands. A number of world-renowned technology companies use the HackerOne platform, such as Yahoo, Twitter, Adobe, Uber, and Facebook. At present, more than 3,000 HackerOne platforms have registered hackers from more than 150 countries, and there have been more than 500 loopholes in the testing of cooperative enterprises. HackerOne was one of the first companies to accept and use hackers to develop business models.
| Business HistoryIn 2011, Dutch hackers Jobert Abma, Michiel Prins, and Merijn Terheggen in their 20s listed out of a list of 100 high-tech companies they planned to invade. They soon discovered Facebook, Google, Apple, Microsoft, Twitter, etc. There are different degrees of security holes in the network systems of other 95 companies. They call this list "Hack 100."
When they contacted these companies, one-third of companies did not pay attention to these issues. Another 1/3 of the companies thanked them but did not fix the loopholes. The rest of the companies are trying to solve the loopholes as soon as possible. Fortunately, no one informed the police.

When dealing with Facebook's loopholes, they met Alex Rice, Facebook's product security manager, and formed a company partner. He founded HackerOne in 2012. Alex Rice served as the company's CTO, Merijn Terheggen as CEO, Jobert Abma as technical leader, and Michiel Prins as product manager. In 2014, Katie Moussouris, former Microsoft Chief Security Strategist (CPO), joined as its CPO. At the end of 2015, Marten Mickos, former CEO of MySQL and Eucalyptus, became the CEO of HackerOne.
| Investment situationIn May 2014, HackerOne received a $9 million Series A investment led by Benchmark; in June 2015, HackerOne received a $25 million Series B investment, led by New Enterprise Associates, with Investors Nicolas Berggruen, Brandon Beck, David Sacks, Jeremy Stoppelman, Drew Houston, Marc Benioff, Benchmark, etc.

HackerOne focuses on information security, and aims to achieve win-win results for both companies and hackers through the establishment of loophole reward platforms between companies and hackers. HackerOne through the establishment of the loopholes in the measurement platform, by the test companies to pay hackers to find rewards for the rewards, HackerOne from the corporate awards to extract 20% of the cost.
In addition, HackerOne also provides companies with paid service models such as vulnerability subscription services, vulnerability disclosure guidance, and security consulting. Currently, HackerOne has helped more than 500 companies find more than 20,000 vulnerabilities and distributed more than 6 million US dollars to more than 3,200 independent security researchers. Individual vulnerabilities have been awarded up to 30,000 US dollars.
| Service methodsFor hackers:
Registered, added projects, and submitted vulnerabilities as usual common measurement platforms;
For companies:
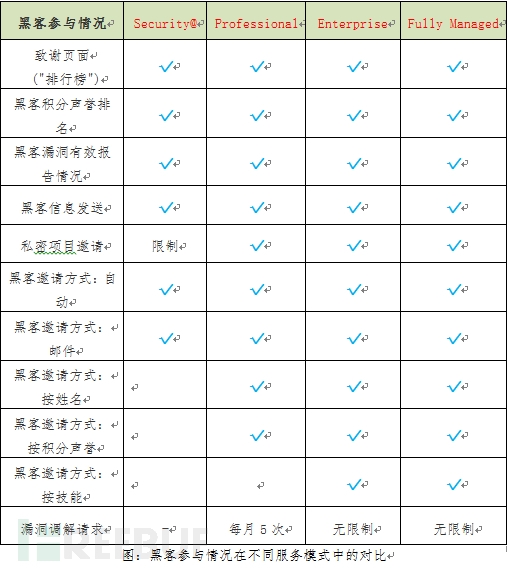
For all companies, HackerOne provides four service modes: Security@, Professional, Enterprise, and Fully Managed. HackerOne provides different services for vulnerability disclosure, vulnerability management, and security in these modes. The following are different service modes. Contrast:
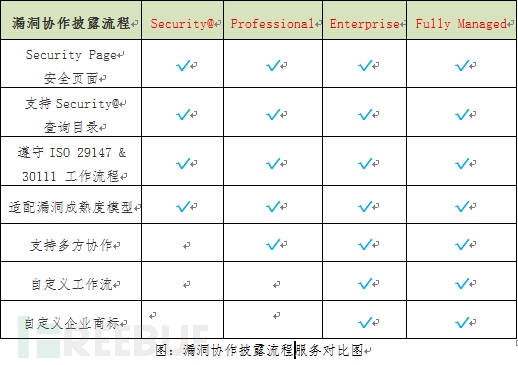

The Security Page page contains key information such as company status, disclosure policies, hackers wishing to invite, vulnerability rules, and more.
Fully Managed is HackerOne's paid service for companies that want to conduct further screening and verification of vulnerability conditions. Through the Fully Managed model, companies can choose to sign unscheduled information security services with HackerOne's world-class security consulting partner.
Security@ is the HackerOne community security project quick query directory. Through this directory, you can quickly find companies that exploit loopholes on the HackerOne platform to facilitate hackers to submit vulnerabilities.
|The principle of confidentialityHackerOne only provides processing tools for the “Vulnerabilities Collaboration Disclosure†project. The website implements vulnerability database access control rights. HackerOne employees have no right to view any vendor vulnerability information. HackerOne never shares the customer's vulnerability data with other third parties and advocates PGP encryption. Submit vulnerability information. Until the vulnerabilities are resolved, all submitted vulnerability information is invisible except for the enterprise and the submitter of the vulnerability.
| Vulnerability award price(1) It depends on the quality of the submitted loopholes. The vulnerability price given by the manufacturer can refer to several aspects: the severity of the vulnerability, the scope of impact on the end user or customer, the project budget, the project phase and confidentiality, and the maturity of the vendor vulnerability disclosure plan.
(2) In order to attract and motivate hackers, HackerOne stipulates that the minimum amount of rewards per hole is not less than $100. For most common vulnerabilities , the range of awards is $100-$1,000. Of course, HackerOne also advocates over-recognizing certain serious flaws. . Considering that different vulnerabilities have different effects on different vendors, for example, Clickjacking vulnerabilities are very serious for some enterprises, but they are only informative vulnerabilities for other enterprises. Therefore, HackerOne does not address the lower limit of 100 US dollars. Different vulnerability categories set the minimum reward limit. The amount of reward depends on the extent to which the vulnerability affects the manufacturer.
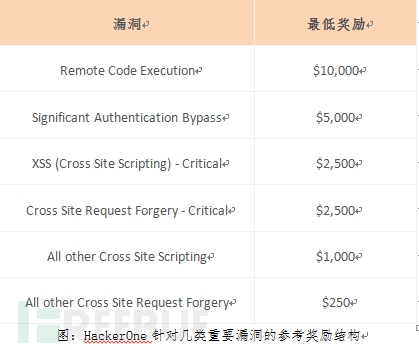
(3) For several types of particularly important vulnerabilities , in order to improve reward transparency and hacking expectations, HackerOne has provided a minimum reward structure for enterprise reference based on vulnerability maturity model. Of course, the company has the right to increase the minimum reward benchmark according to the degree of vulnerability impact. . For example, Uber's XSS vulnerability has recently reached $7,000.
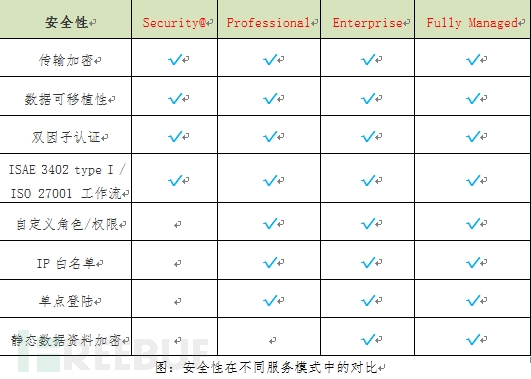
(1) All information exchanged with the Hacker One server platform is encrypted. The security team can use HackerOne's IP whitelisting policy for access control.
(2) HackerOne uses military-grade encryption technology, two-factor authentication, single sign-on, and ISO/IEC 27001 information security management system certification;
(3) HackerOne advocates companies to comply with ISO/IEC 29147-2014 "Information Technology - Security Technology - Vulnerability Disclosure Standards" and at the same time help guide enterprises to conduct vulnerabilities disclosure through an automated platform. The purpose of the ISO/IEC 29147-2014 standard is to provide enterprises with guidelines on how to receive vulnerabilities and issue vulnerabilities solutions, and to provide enterprises with relevant information and examples of vulnerabilities disclosure processes.
| Featured DASHBOARDHackerOne's Dashboard feature is designed to display accurate information about the company's submission of vulnerabilities and rewards. Dashboard can also help companies identify and track areas of improvement in the software development life cycle. Through Dashboard, companies can view daily, weekly, and monthly vulnerability trends and developments. Data-generated reports can be downloaded in CSV format. In addition, if companies need more advanced and timely reporting requirements, they can integrate Dashboard data into third-party reporting tools through HackerOne's API.
Dashboard's data metrics include: the number of bugs to be resolved, sum total of rewards, hacking acknowledgements, number of reward reports, average bonuses, percentage of payment and vulnerability resolution, vulnerability response time, vulnerability resolution time, report status diagram, vulnerability response, and resolution Time status chart, bonus payment chart, hacker acquisition amount ranking chart, hacker award ranking chart.

HackerOne has published a Vulnerability Coordination Maturity Model (VCMM) for vulnerability collaboration disclosure based on long-term vulnerability submission model analysis. HackerOne believes that the factors affecting the collaborative disclosure of loopholes include five areas of competence: organization, engineering, communication, analysis, and incentives. Each area includes three levels of maturity: basic, advanced, and expert. The VCMM model aims to help companies. Evaluate the loophole coordination mechanism, visually identify the areas that need improvement, guide the company to enhance the internal and external organizational capabilities, and better eliminate potential safety hazards.
HackerOne's VCMM publicly-oriented test model for the community is: VCMM-survey, of course, in addition, HackerOne also provides targeted measurement companies in their platform cooperation to provide quantitative information model of vulnerability information. The following is a ranking of VCMM's five competence areas:



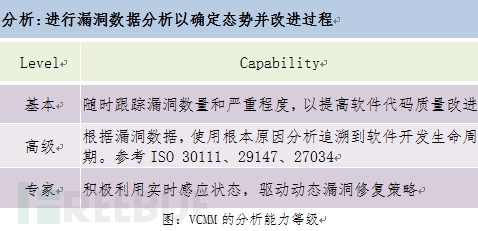
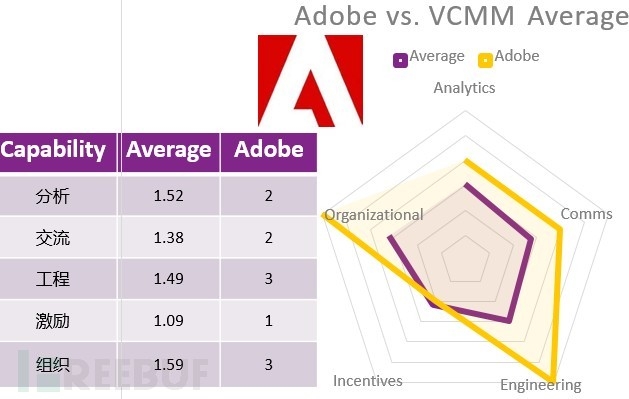
According to the competency area scores in the five aspects, VCMM can determine the problems that enterprises have in the management of loopholes and areas in urgent need of improvement. For example, the following is a VCMM model diagram of Adobe at a certain period.
HackerOne declares the following vulnerability disclosure principles: All technologies contain loopholes. If you find a security hole, we hope to help you. Submit a vulnerability or register as a test company through the HackerOne platform project. We hope you read and agree to the following guidelines.
(1) Disclosure philosophy
We believe that the mutual respect and transparency between vulnerability discoverers and all test companies are prerequisites for an effective vulnerability disclosure process.
The submitter of the vulnerability must: respect rules, respect privacy, be patient and friendly;
All measurement companies must: safety as the most important, respect for the loophole submitter, reward loophole submitter, and friendliness.
(2) Vulnerability disclosure process:
The contents of the submitted vulnerability report will be immediately provided to the testing company's security team. In a non-public state, the company will have enough time to verify the vulnerability and issue a patch bulletin. Public disclosure can only occur after the vulnerability submission report is closed.
General situation: If neither party raises an objection, the contents of the vulnerability submission report will be made public within 30 days.
Agreement between the parties: We encourage loophole submitters and companies to have good communication and negotiation regarding the deadline for disclosure. If there is no objection, the disclosure time can be determined according to the negotiation time.
Protection Disclosure: If a company finds that the submitted vulnerability is being actively exploited and harmed to the public, the company may immediately issue a bulletin bulletin to the community so that the user can take protective measures.
Extension: Due to factors such as complexity, some vulnerabilities will need to be repaired for more than 30 days. In this case, the vulnerability report will continue to be kept confidential to ensure that the corporate security team has enough time to solve the problem. At the same time, we encourage the corporate security team to maintain communication with the vulnerability submitter.
The last resort: If within 180 days, all testing enterprise security teams are unable or unwilling to provide an exact vulnerability disclosure schedule, the submitter of the vulnerability has the right to disclose the content of the vulnerability. We believe that in this extreme situation, maintaining transparency to the public is the best way.
| Horizontal comparison of HackerOne and other platformsIn August 2015, Penn State University conducted several researches and analysis on several well-known loopholes, including the number of vulnerabilities submitted by all platforms, registration of white hats, cooperative customers, and vulnerabilities. Domestic platforms are also included. The following is a comparison chart of various indicators of HackerOne:

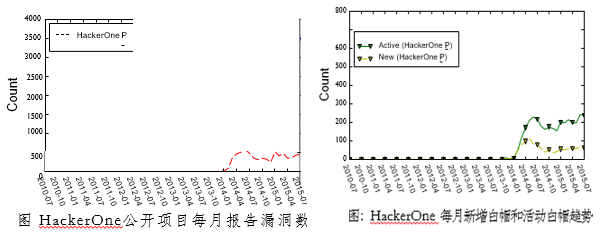
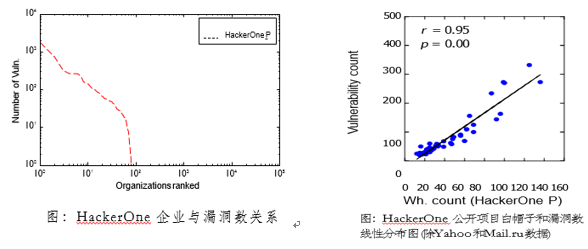
From the above indicators, it can be seen that the number of white hats on the HackerOne platform has been growing slowly since the company was founded. In addition, only a very few organizations have obtained more loophole reports, such as twitter and facebook, etc., which are rich and domineering. From the linear charts of white hats and loopholes, it can be seen that there are more elite hackers on the HackerOne platform, some hackers are active on the platform for a long time, and the submitted loopholes are of high quality. The results of the study indicate that the number of white hats in China's public measurement platforms is relatively large and relatively active. However, compared with foreign test platforms, the gap between bonuses and bonuses is relatively large and remains to be improved.
| Personal point of viewSecurity and confidentiality: HackerOne only provides vulnerability reporting, processing, and consulting platforms. HackerOne can not access the information of all tested enterprise vulnerability without authorization, and the content of the submitted vulnerability will not be disclosed until it is completely resolved. The most important point is that the HackerOne platform uses encryption to exchange information and protect white hat information to the greatest degree;
Vulnerability Bonus: From the minimum bonus of 100 kilograms, the old Americans' emphasis on security can be reflected in the first place. In addition, the reference reward structure given by HackerOne for several important vulnerabilities is also quite attractive for white hats. Such as XXS (critical) and CSRF (critical) type vulnerabilities can reach 2,500 knives, all XSS type vulnerabilities are 1,000 knives, although only reference, but if the company's minimum award amount does not meet this standard, then the enterprise trust and public Measuring the attractiveness will be affected, of course, the enthusiasm of the white hat will not be too high. For example, Uber's XSS vulnerability has recently reached 7,000 US dollars. According to the HackerOne platform, some senior hackers claim that they earn more than 200,000 US dollars each year, and a single vulnerability has reached 30,000 US dollars.
Professional compliance: Most of the vendors participating in the survey are well-known and innovative companies in the industry. The market share of these companies requires that companies must pay enough attention to safety. Of course, apart from agreeing with HackerOne's disclosure policy, these companies are HackerOne's test items also have their own rules, such as vulnerability effectiveness, vulnerability report templates, and vulnerability testing rules. As white hats, HackerOne will regularly evaluate the effectiveness of the submitted loopholes, combined with credits and other points of appreciation, as a white hat's rank reputation, and also serve as an assessment indicator for certain invited items.
Legal definition: This may be a problem faced by domestic and foreign public test platforms. First of all, companies that participate in the HackerOne test program must comply with HackerOne's disclosure rules, so that HackerOne, companies and white hats jointly endorsed testing projects to maximize the protection of white hats; in addition, HackerOne believes that the Internet world is the frontier of future information warfare. Positions, and hackers are soldiers and weapon makers, how to win or recruit hackers to participate in defense may currently need to amend existing laws to eliminate the ambiguity between “security protection†and “crime†and encourage security research. HackerOne believes that white hats use scarce and valuable technology to find information to protect vulnerability. This is in itself a matter for the benefit of businesses and the public. If white-hat security personnel can find loopholes, other bad guys can also find out, but the current US computer laws have not yet Give clear protection to white hat security researchers.
After the U.S. information security community filed an amendment to the exemption clauses for security research in May 2015, the U.S. Copyright Office amended the Digital Millennium Copyright Act to include a disclaimer on software security research. This may be an improvement in the future of loopholes. HackerOne hopes that security research can be legally protected by law and calls for current and future legal systems to create a good research atmosphere for security researchers.
User Experience: Overall, HackerOne's user experience is still quite good. From the aspects of registration, submission of vulnerabilities, information reception and project invitation, etc., it can stand in the white cap and the enterprise's perspective to provide services and consider issues; In addition, exchanges, incentives, and loopholes between white caps and companies are relatively timely, transparent, and open. Second, the HackerOne website architecture can also reflect the good user experience features HackerOne has.
The above is a brief introduction and analysis of HackerOne. In comparison, the development of domestic measurement platforms is also quite good. As far as domestic test manufacturers are concerned, the author is familiar with the vulnerability box. From the feedback of the effectiveness of the corporate customers on the measured services and the rapid increase in acceptance in recent years, the existence value of the public measurement platforms is beyond doubt.
Just like HackerOne CEO Marten Mickos said, the future of the loopholes measurement platform is full of vitality. Of course, the well-tested ecological development of the public needs the importance of social information security, corporate responsibility, white hat skills, policies and regulations. Improve and enhance. As a white hat, while we are striving to improve our skills, we must not forget to join the domestic excellent measurement platform to contribute our own meagre strength to information security.
Lei Fengwang Note: The author of the cloud, this article is FreeBuf original reward program, posted by Lei Feng network release, transfer the situation contact authorization, and retain the source and the author, not to delete the content.
Bimetal Dial Thermometer,Bimetallic Actuated Thermometers,Bi Metal Stem Thermometer,Bimetal Strip Thermometer
Changshu Herun Import & Export Co.,Ltd , https://www.herunchina.com