[Global Network reporter Wang Nan] WannaCry blackmailed and attacked China at about 20:00 on May 12. Up to now, there have been serious damages to mainframes such as central enterprises, hospitals, schools, energy, government agencies, etc. Although the Central Internet Information Office externally stated that the speed of transmission has slowed down, the panic continues.
In response to WannaCry’s arrival, various anti-virus and network security vendors are fighting all night and are active. At present, there are two main ways to see everyone: The first is to close port 445; the second is to patch.
"These two methods are relatively passive, and their effects and effects are limited." After the reporter contacted Jinshan Security at the first time, the head of the big data center said so.
Only playing patched ports can not completely eradicate blackmailers
Why is the WannaCry blackmail virus spreading so fast this time? According to the person in charge of the Jinshan Security Big Data Center, the main reason is that the exploiters use high-level vulnerabilities.
The first is that this WanaCry ransomware exploited the SMB protocol vulnerabilities in MS17-010. This protocol vulnerability was defined as the highest severity level in Microsoft's official vulnerability disclosure, and the exploitability was "remote execution of malicious code".


More critical is the impact of this loophole, basically covering all Windows operating systems.
The second reason is that although Microsoft has released a patch for this vulnerability in March of this year, malware makers took full advantage of the timing of people's patching delays, and there were drills to advance the sampling of the global vulnerability scan, confirming this vulnerability. The situation that has not yet been repaired has led to a very precise and effective launch of a global scale blackmail attack.
Is it okay to finish the patch?
Up to now, various types of manufacturers in the market have introduced various kinds of immune tools, repair tools, emergency tools and even killing tools. The core function of these tools is to help users patch. "Patching is necessary, but patching can only reduce the chances of getting in the game and the ability to spread it, and it cannot completely cure it." Jinshan Security experts said: "No one dares to promise: a patch can completely prevent the extortionist virus." Some of the tools are quite useless. This is the most intuitive result of Jinshan Security's testing of various tools.
Seal 445 ports have no use?
"The 445 is innocent." Jinshan Security experts said: 445 port is often used as a port for file sharing and printer sharing. However, this incident uses the SMB protocol vulnerabilities instead of opening 445. Although SMB uses 445, port 445 is innocent. Many companies directly closed the 445 port for convenience. Closing port 445 can reduce or reduce the spread of WannaCry worms in the LAN, but it cannot solve the issue of whether a single host is a ransomware virus, let alone a radical cure.
The "millisecond master defense" model is a magic weapon against extortionists.
"The fierce first wave of users responded and we were stunned by Jinshan," said Li Yuan, head of Jinshan Security's business, to the reporter. The data shows that: As of now, Jinshan Security has not yet suffered from the infringement of WannaCry's ransomware after an enterprise-level and client-side user has not installed the product.
Jinshan Security has achieved such an excellent record. The main reasons come from two reasons. First, from 2015, Jinshan Security is studying the defense program of the ransomware virus. Its HIPS-based "active defense and reinforcement" technology for the ransomware virus can dispose of and shut down the ransomware virus in violation of the millisecond level. It is precisely because of this proprietary patent technology that it supports Jinshan Security to assist users in achieving the first phase of the goal of curbing the WannaCry ransomware virus.
The second reason comes from the rapid response of Jinshan Security. From 20:00 in the evening of May 12, Jinshan Security has been fighting for nearly 72 hours. Jinshan Security, including product, technology, and operation and maintenance personnel, has been fighting all night. They have formed various types of security testing and defense tools, and conducted various tests in different customers' different environments to ensure safety.
"We can kill and dispose of the entire family of extortionists that may have existed and may appear in the future, not just WannaCry." Kingsoft said that they can defend against a large number of different forms of extortionist software family Among its variants are the discovery of the earliest CTB-Locker, and Locky, which had a large-scale outbreak and made waves, including Cerber, Crysis, CryptoLocker, CryptoWall, Jigsaw, KeRanger, LeChiffre, TeslaCrypt, TorrentLocker, ZCryptor, and others. The ransomware virus.
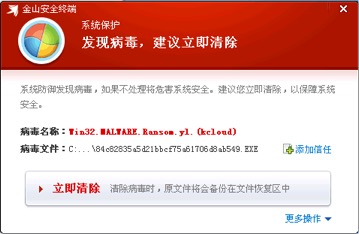
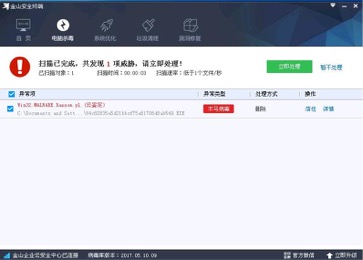
The outbreak of the WannaCry blackmailer virus is the biggest cybersecurity incident China has faced in the past 10 years. For domestic anti-virus software vendors, the WannaCry ransomware virus is a touchstone to test whether products can support users to achieve defense, product technology is to pass. After the outbreak of the incident, many companies exposed the original speculation that they had been frequently hyped and did not attach importance to products and technologies.
The person in charge of the Jinshan Security in the interview once again stated that there is no need to panic about WanaCry and that a good product can have a strong defense. When WanaCry invades Chinese users, we are willing to stand by our users and always ensure safety.
BIOTEPT NEMA Rolled steel standard high starting torque, high slip ratio three-phase asynchronous motors B design have insulation class F, Protection grade IP44, service factor 1.15. Voltage rating of 230/460V. The rated frequency is 60HZ.


Premium Efficiency Motor,Nema Premium Efficiency, Ie4 Electric Motors,A 3 Phase Induction Motor
Ningbo Biote Mechanical Electrical Co.,Ltd , https://www.biotept.com